CDP:Backnet Pattern
Establishment of a Management Network
Contents |
Problem to Be Solved
The servers that are open to the Internet and that are accessed by a large number of non-specific users (such as web servers) are often accessed through that same network interface for the purposes of management. However, when a high security level is required, this is problematic because use of the same network interface as access that cannot be trusted should be avoided, meaning that you should separate these interfaces.
Explanation of the Cloud Solution/Pattern
A technique that is often used in structuring and managing ordinary systems is to provide multiple network interfaces on a web server that is open to the public, to separate the Management Network Interface from the public network interface. The provision of the Management Network Interface is known as a "Backnet," and the provision of this Backnet can reduce the network risk in management.
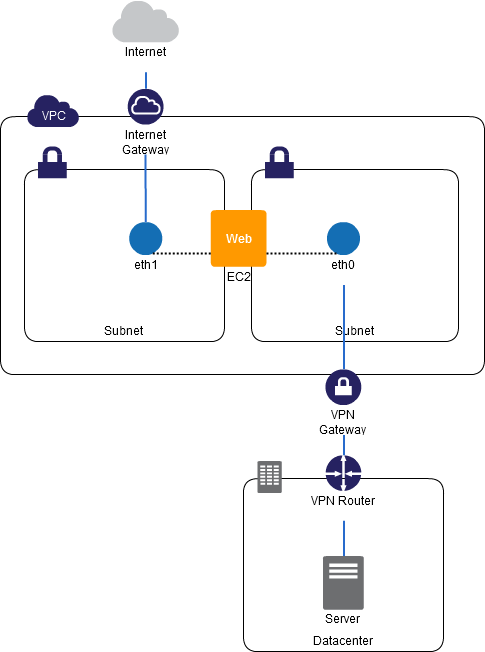
Implementation
In a Virtual Private Cloud (VPC), you can use two virtual network interfaces or "Elastic Network Interfaces" (ENI) for an EC2 instance. One is set up as a public network interface, and the other is set up as an Management Network Interface.
- Install a web server or database server on an EC2 instance and prepare the two ENIs (outward-looking and inward-looking).
- Have one of the ENIs belong to the public network of the VPC and route 0.0.0.0/0 (all traffic) to the outward-looking Internet gateway.
- Have the second ENI belong to the private subnet of the VPC, and route 0.0.0.0/0 (all traffic) to the VPN gateway that is connected to, for example, the company intranet. Use this also for SSH access and management/logs.
- Because you can provide a separate security group for the individual virtual network interfaces, set up the one virtual network interface so as to allow traffic on Port 80, and the other network interface so as to allow traffic on Port 22.
Configuration
Benefits
- Because there is no port for the outside Internet that can be accessed as SSH, security is high.
- There is a clear distinction between the outward-looking and inward-looking virtual network interfaces, preventing errors in procedures.
Cautions
- Because you also have to set up a virtual private network (VPN), the operating cost will be somewhat higher.
