CDP:Operational Firewall Pattern
Controlling Access by Individual Function
Contents |
Problem to Be Solved
When the scope of a system is large, there will be multiple organizations for performing development and maintenance. For example, you may have a division between the company that performs system development and the company that performs log analysis and operation/monitoring. When defining rules for firewalls for groups of individual functions, if there is a change in the access origin, or if access itself becomes unnecessary, you will need to update the rules that have been grouped by the functions. Not only does such setup work take time, but it interferes with the possibility of performing centralized control of which organization can access which system.
Explanation of the Cloud Solution/Pattern
In the past, firewalls have used dedicated machines, and rules were also grouped together by function and written (controlled).In the AWS Cloud, the firewall is virtualized, enabling a more flexible setup. The rules can be grouped and set or applied to servers by group units. Having these units known as groups be organizations enables centralized control of the setup regarding organizations.
Implementation
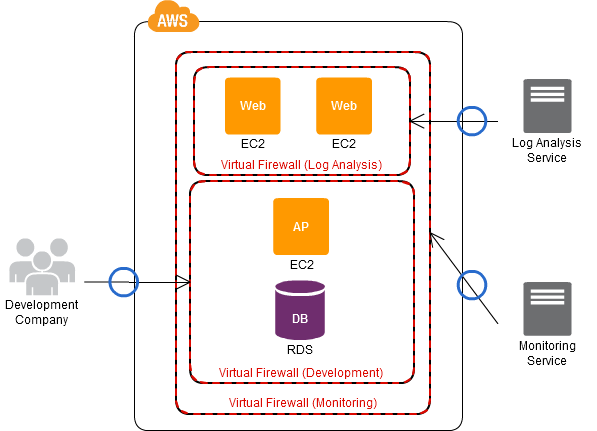
Because you can create multiple security groups, you can create a security group for each organization, enabling centralized control of rules for individual organizations. For a Virtual Private Cloud (VPC), you can set up the virtual firewall to apply or not apply to the EC2 instances that are running, making it possible to turn them on or off as necessary.
- Create a security group for each organization, such as the development company, the operating company, and so forth.
- For each security group, perform the setup (of the access origin, the access ports, and the like) depending on the group (organization).
- Apply the security groups to the EC2 instances.
Configuration
Benefits
- This lets you have centralized control of access information for each accessing organization.
- This can reduce setup errors when modifying access control.
- You can use this together with the Functional Firewall Pattern.
Cautions
- In virtual firewalls, control mainly uses the connection origin IP address, rather than the organizational functions of ordinary users. Because of this, control by individual users requires implementation on the operating system or application layer.
